For the latest version: http://that1archive.neocities.org/subfolder1/gchq-cryptome-slide.html
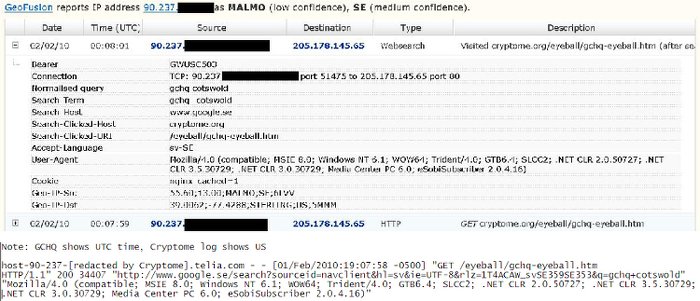
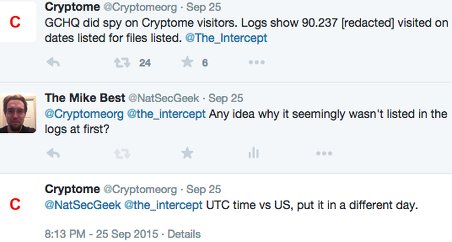
A few days ago, a new Snowden slide was released that appeared to show that the GCHQ was monitoring Cryptome in near-real-time by examining the browsing data of one of the websites' visitors. John and Deborah of Cryptome later verified that the information in their slides matched their logs, seemingly verifying the legitimacy of the slide itself and the information presented about KARMA POLICE.


However, after examining the slide and all the information available, I realized that it was possible to create the slide (or one like it) with accurate data without any of the sources cited/assumed/alleged. To demonstrate this, I put together some comparable information. To respect the privacy of visitors to Cryptome, the end of each IP address is redacted and I've provided only a little information about several users instead of focusing on one user to provide detailed information about.
A few notes before getting into the data:
IP: 212.48.158.*
Date: 2010-02-10
Time: 23:06:15
URL: http://cryptome.org/cartome/foucault.htm
Note that I manually translated the time and date from a time code, so it may be slightly incorrect. The original timestamp was 20100210230615.
In case I mistranslated the timestamp or anyone thinks that it was a fluke, here are twelve time and dates along with the redacted IP address that visited Cryptome at that time. These time and dates were originally rendered in a human readable format, so there is no danger that I mistranslated them.
Finally, a semi-obscure phrase from the that was put into a search engine - complete with the original typo.
"architectural engineering in miidle east" - it may appear in the logs as "architectural+engineering+in+miidle+east"
All of this information should be readily verifiable by John and Deborah at Cryptome, demonstrating that each of the pieces of the slide could have been created without the benefit of a surveillance program or large budget. In other words, the guilty knowledge implied by the accuracy of the slide can imply things other than being guilt of surveillance.